TryHackMe - Lay of the Land - Post Compromise
TryHackMe - Lay of the Land - Post Compromise
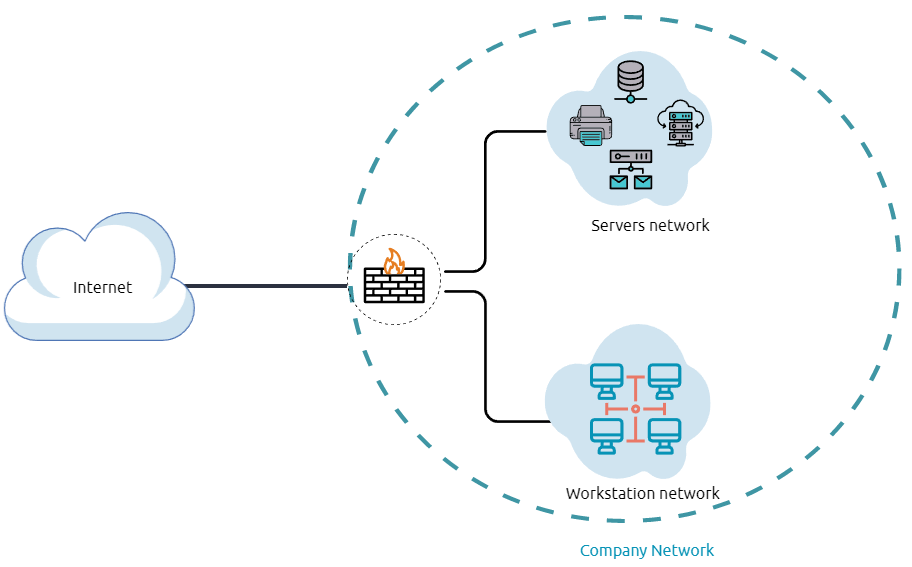
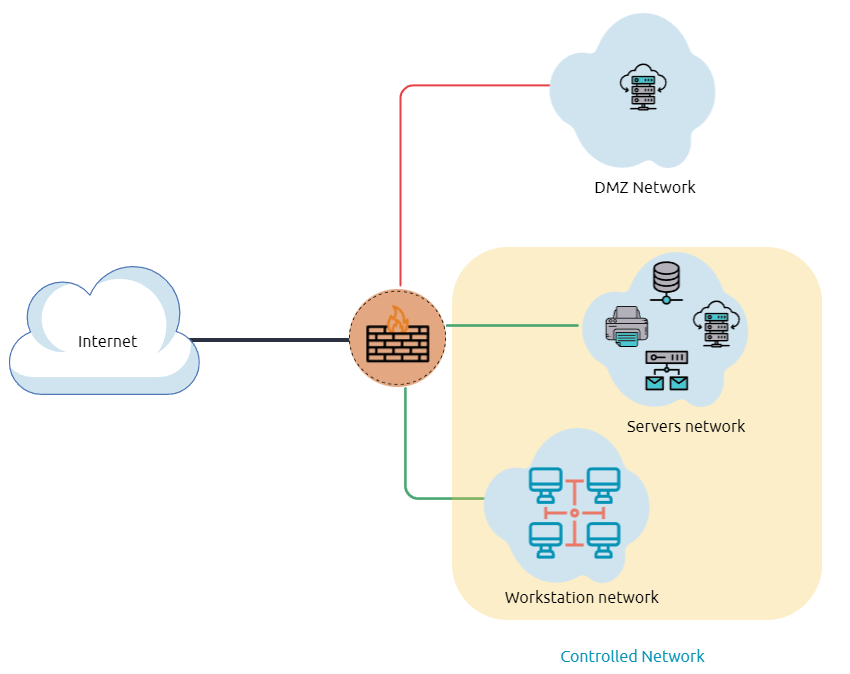
Internal Network:
A Demilitarized Zone (DMZ)
Network Enumeration
1
2
netstat -na
arp -a
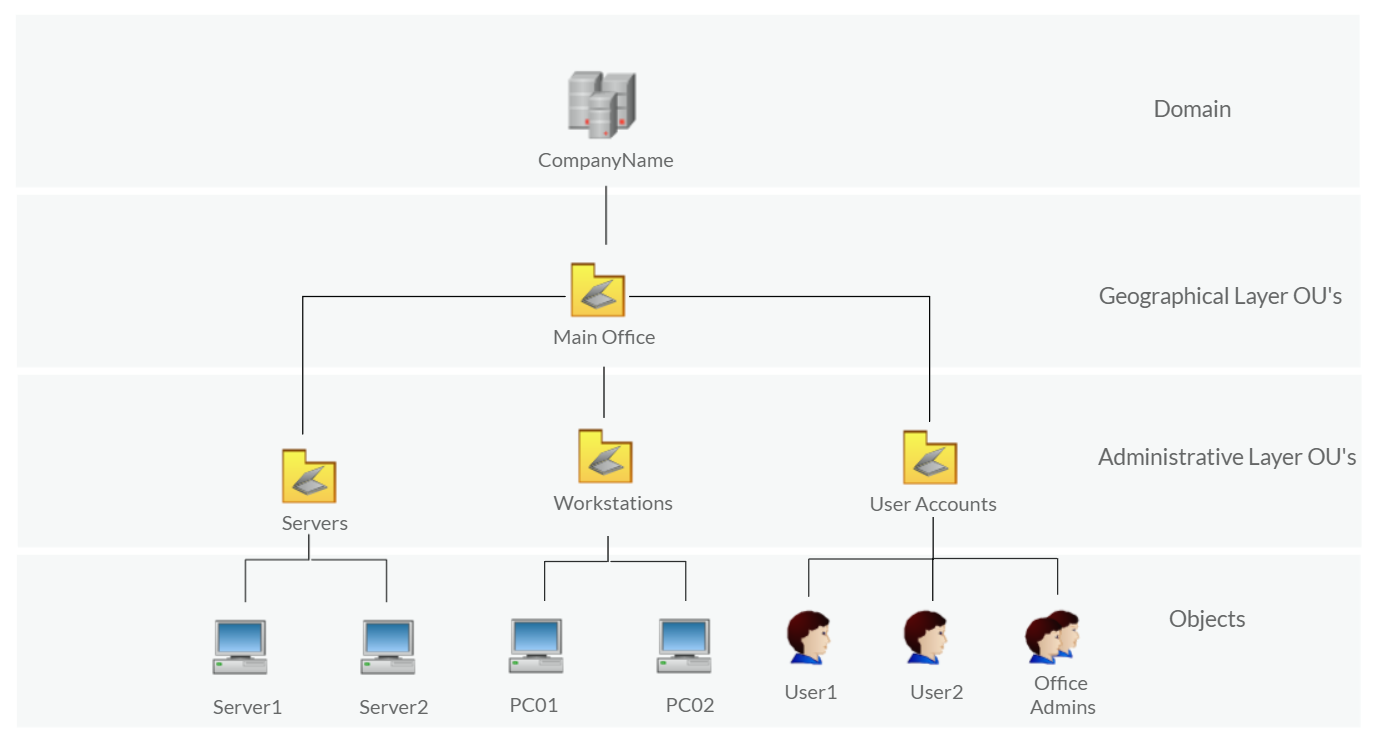
AD - Environment
Components of AD
List of Active Directory components that we need to be familiar with:
- Domain Controllers
- Organizational Units
- AD objects
- AD Domains
- Forest
- AD Service Accounts: Built-in local users, Domain users, Managed service accounts
- Domain Administrators
Checking for AD
1
systeminfo | findstr Domain
Admin Groups
| | | |—|—| |BUILTIN\Administrator|Local admin access on a domain controller| |Domain Admins|Administrative access to all resources in the domain| |Enterprise Admins|Available only in the forest root| |Schema Admins|Capable of modifying domain/forest; useful for red teamers| |Server Operators|Can manage domain servers| |Account Operators|Can manage users that are not in privileged group|
AD Info
1
Get-ADUser -Filter *
1
Get-ADUser -Filter * -SearchBase "CN=Users,DC=THMREDTEAM,DC=COM"
Host Security Solution - Info
- AntiVirus
1
wmic /namespace:\\root\securitycenter2 path antivirusproduct
\(or\)
1
Get-CimInstance -Namespace root/SecurityCenter2 -ClassName AntivirusProduct
- Microsoft Windows Defender
1
Get-Service WinDefend
\(or\)
1
Get-MpComputerStatus | select RealTimeProtectionEnabled
\(or\)
1
Get-NetFirewallProfile | Format-Table Name, Enabled
1
Get-NetFirewallRule | select DisplayName, Enabled, Description
- Threat Details
1
Get-MpThreat
Checking Network Firewall - Allow and Deny
1
Test-NetConnection -ComputerName 127.0.0.1 -Port 80
Security Event Log
1
Get-EventLog -List
System monitor
1
Get-Process | Where-Object { $_.ProcessName -eq "Sysmon" }1
reg query HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\WINEVT\Channels\Microsoft-Windows-Sysmon/Operational
Installed Applications
1
wmic product get name,version
Hidden Dir:
1
Get-ChildItem -Hidden -Path C:\Users\kkidd\Desktop\
Processes:
1 2 3 4 5
net start wmic service where "name like 'THM Demo'" get Name,PathName Get-Process -Name thm-demo
- AntiVirus
This post is licensed under CC BY 4.0 by the author.